Software manufacturers, utility companies, hotels, law enforcement, banks, government agencies and criminals all stand to gain from you surrendering your privacy.
They are all selling the lie that you must be a drug dealer or a terrorist if you prefer to communicate anonymously.
It’s brainwashing. Don’t be a sheeple. Good guys value privacy too.
Americans have traditionally valued privacy very highly. Many still do. Many have “voted with their feet” and moved to less densely populated Western states and Alaska.
“The Greatest Generation” and those who lived through the great depression counted privacy among our inalienable, God-given rights. Americans stood united on the issue from the founding fathers right up until “generation x”.
It’s pretty easy to spot when privacy began its cycle of demise.
But what changed? What initiated the down-hill slide? Why was this cherished fundamental of the American dream devalued? How did we lose our grip on it?
These questions affect us all. Many factors joined forces to wage war on privacy, and now it’s our turn to fight back taking these seven steps to protect our privacy.
1. Implement Strong Physical Security
Ever heard that possession is nine tenths of the law? All jurisdictions recognize that you have rights regarding your home or place of residence. Make use of them. They are barrier to those who abide by or at least fear the law. For the rest, you need to make sure your property is not a worthwhile target. Don’t leave physical deterrents out of the privacy equation.
On the technology side of the equation, you might have decent security and SOP in place. No passwords written down anywhere near the computer.
But if someone gets into the same room with your computer, there are any number of ways to penetrate that security. They could install a keystroke logger that makes a note of your every keystroke. So do due diligence in regards to physical security.
2. Encrypt, Encrypt, Encrypt and Encrypt Some More
Encryption is one of the very best tools in your arsenal. As long as your data is properly encrypted, even if all your other security measures fail, no useful information will come out of the encrypted data … period, end of story.
If you only take one single piece of information away from this steps, make sure it’s to create effective data encryption SOP and follow it to the letter.
If you do this one thing, even if your enemies descend upon your home like the US Military on Bin Laden or put crime tape around or bag everything and every property you own, they won’t get a shred of useful data.
They will have to rely purely on external, largely circumstantial, sources of evidence.
3. Don’t Adopt New Technology Prematurely
Choose not to adopt emergent technology until security bugs have been found and patched and you understand how the new technology will impact your privacy.
There are many reasons not to adopt these new technologies prematurely:
- You pay a premium to be on the “bleeding edge” of technology.
- Why beta-test (troubleshoot) a manufacturer’s new product for them? Waiting until the first round or two of patches or revisions have been made ensures a more robust platform.
- Many new products are highly proprietary when they first hit the market so you will be locked in to the options offered by the manufacturer. Once the other manufacturers have time to respond, you will have far more options to customize the product to your needs, resulting in a superior solution.
- Lastly and most important to this course, it’s much safer to adopt a technology after it has been poured over and reverse-engineered by privacy experts and they have published their findings.
4. Don’t Create New Online Accounts that Hamper Your OPSEC
Delete any that you already have submitted. How many accounts do you have with email services, search engines, banks, investments, utility companies, internet service providers, credit cards, social media, shopping, schools, organizations, backup services, file sharing, software developers, app stores, entertainment, games or other types of websites online?
And how many of them do you use on a consistent basis?
Remember that every account is a potential OPSEC liability. Learn how to decrease your exposure when you do create accounts.
Some of you may want to get rid of any accounts you created before you learned how to create them and use them without creating undue vulnerability.
5. Configure Your Technology’s Privacy Related Settings
Configure content and settings of hardware, software, apps and accounts to reflect the level of privacy you desire and don’t choose hardware, software, apps or accounts that will affect your privacy in ways that are unacceptable to you
If you participate in social media using your real name and information, you are volunteering all kinds of information to anyone who’s interested.
If your employer or a potential employer, employee or anyone else for that matter looks up information that you voluntarily posted to social media sites that you participate in, that’s on you. You put it out there for everyone to see.
Many websites and developers are now at least paying lip service to privacy because folks like us are making a lot of noise about the issue and it’s costing them brand equity which translates into money. The result is that privacy settings and privacy statements have come about.
We’ve argued long and hard for them, so use them. Read the statements and third party security reviews to discern which features and settings of your hardware, software and sites you use will make a difference.
In many instances, you may need to stop using them and use a competitive product that values your privacy or at least recognizes that the concept still exists. Invest the time to understand and configure your technology’s privacy-related settings to protect and limit distribution of your information as opposed to volunteering as much information as possible.
Make use of technology as a tool to effect change on a large scale. Lastly, take into account who each device, software, app or account is created by, their privacy philosophy, where they are physically located, and what jurisdiction it falls under.
The Homeland Security alphabet soup might squeeze American companies left and right or accuse them of being unpatriotic if they don’t grant unfettered access to email accounts but that’s not as easy to do in another countries.
Some US agencies even infiltrate large companies someone deems vital to national security. They recruit employees to spy for them. This is not exactly top secret knowledge. But that’s not as easy to do in other countries, especially in countries that take a dim view of recently exposed US espionage activities.
6. Delete or Destroy
If you ever have to defend your life with a firearm in the US, you will likely have to defend yourself again in court.
Once you’ve fulfilled your responsibilities of informing the authority and calling for assistance if your attorney was standing to the side and saw the whole thing, he would probably walk over to you and staple your tongue to the roof of your mouth.
He would do it to shut you up because he knows that the burden of proof is on the prosecution and he wouldn’t want you saying anything that might make the prosecution’s job any easier. He would do it even if he was certain you were innocent because he wouldn’t want to give the other side any more resources to work with than they already have.
The same principle applies to privacy, and everything, not just computer files. Crosscut shred paper, redact everything else. If you need to submit receipts for reimbursement, they might need to see your name and the amount, but do they need your credit card billing address or confirmation numbers that might yield more information?
When it comes to information, get rid of anything and everything you don’t need, especially data or computer files of any kind. Give the following criterion a try: if it’s not beautiful, useful or cherished, get rid of it.
Think of it as giving whoever is after your information less to work with. Sanitize everything you can obtain access to as long as you don’t have to break any laws to do so. The more unnecessary copies of data you have laying around, the more complicated the task of managing and securing them will become.
When it’s time to get rid of sensitive information, don’t just delete it or format the drive and throw it in the trash or give it away. Data can be extracted from many storage media even after it has been deleted or the drive has been formatted.
The storage device must be destroyed using data destruction protocols. Destroy the hard drives, SSD’s flash memory, magnetic or optical and any other durable storage medium in such a way that makes the data unrecoverable. Memory technology is constantly in a state of flux.
Different methods are used to destroy a hard drive that stores data on a magnetic medium than a solid state hard drive or an optical disc or a tape drive and so on. It’s a simple matter to look it up or we can go into more detail in a more in-depth course. The important thing to take away here is to research how to destroy the data on the device before attempting to destroy it.
Do not simply destroy it. If you need to destroy data in a hurry, there are ways to do that. Systems can be created where you can literally “push a button” and walk away, but they usually involve the release of a large amount of energy in the form of heat and light and are noisy.
Video first seen on Snocrash.
7. Remove or Change Sensitive Information from Databases
By law, many businesses must remove your information from their databases if you request it. The largest, most-used non-governmental databases are maintained by large, legitimate businesses. Their internal SOPs require employees to obey the law.
If they didn’t, they would expose themselves to huge liabilities, and by law, they must remove you from their database if you request it.
Opt out. You didn’t make your digital breadcrumb trail in a day and you’re not going to get rid of it in one. Get your identity squared away first and create a new email specifically for this purpose. Choose a secure email provider from those recommended or find one that meets your needs. Don’t use that email for anything else but getting removed from email lists.
Many will let you remove yourself without requiring a pound of flesh. Click and you are out. Others will make you email them so they can email you back with a link that will enable you to remove yourself from the database, that’s where this email will come in handy. They may ask you to send an email requesting removal and will email you the link that will enable you to remove yourself from their database, so it will be more believable if the email resembles your name in some way.
I doubt you’ll come under scrutiny if the name of your email has nothing to do with your name, but it’s a thought. Some companies will demand to see ID. It’s a process, not an event, but it’s worth it.
What you can’t delete or encrypt can often be changed. The vast majority of search techniques search only the most current data available in order to avoid reporting incorrect, information because it’s useless for most purposes. So changing the information, effectively overwrites it in most databases for most purposes.
You need to decide to whom you will give real information and to whom you will give misinformation. In life and as you take steps to improve your privacy, companies will ask you for information. They will turn around and give it or sell it to all of their parent or sibling corporations, affiliates and pretty much anyone with a dollar in their pocket. Direct marketers buy lists of information all the time.
If you conduct a business today, you are asked for sensitive information at every turn. If you refuse to give information, it will create a very awkward moment that gets you noticed at the very least and in many cases they will refuse to do business with you or remove your name form their list if that’s why you’re contacting them.
I strongly caution you against giving false information to the government, commit identity fraud by using another person’s identity or committing credit fraud by lying on a credit application.
You can provide misinformation without breaking any laws, just be mindful of the law. After all, if you’re giving it up, you’re giving up your rights.








HH | October 25, 2016
|
Excellent article.
Sadly, in this day and age if you want true privacy you need to spend the appropriate time to initialize your selected protocols, after which you must study the program you’ve selected to ensure it meets your needs, implement the program (s) then monitor the program to ensure its continual running within optimum parameters.
Plus (!) you need to remember to turn it on/off when or if you need it.
The upside to all this newfangled security is that once you’ve become accustomed to using it, the whole shebang becomes second nature and a part of your “normal” lifestyle.
Not a bad tradeoff in my book but the initial expenditure of time can be daunting, especially if you are, for all intents and purposes, a casual computer user (i.e., pay bills online, surf the net for movie times or a new restaurant to try, look at the latest Paris fashions, etc.).
But if your business or personal lively hood requires a continuous use of electronic devices and media, you put all that you do at risk for interception by some unfriendly foe, and that can cause you much more than a minor inconvenience.
Lastly, if you believe that taking precautions such as discussed in the article will evaporate any telltale sign of your existence or passing, you might want to think again.
Getting truly “off the grid” is a near impossibility in this day and age. As often as satellites comb the surface of virtually every square meter of this planet and such data is downloaded and saved, when you think about the sophistication and resolution of those cameras, do you REALLY believe you can evaporate and disappear?
I hardly think so.
Somewhere, sometime, you’ll need supplies. Or medicine. Or a part for your solar energy system.
SOMETHING.
And when you come up for air, so to speak, IF you are being looked for, you WILL leave a footprint, so to speak, which is a clue.
Sure, you could, literally, move into a cave but what about the aforementioned items above?
Even living in the forest with heavy tree cover. Those solar panels need exposure to function.
I’ll quit droning on and on.
My point is that you can do a LOT of things to minimize your exposure in a number of ways, many outlined in the article. And you SHOULD, too.
The question is: how much and how FAR do you need to take the topic?
Only YOU can decide and take appropriate action (s).
Good Luck.
Cache | December 16, 2016
|
It can be a daunting task, especially since tech is always changing. You just have to determine what is reasonable for you. If could get people to do just 2 things to protect themselves, I would say to focus on SOP and compartmentalize.
Cache | December 16, 2016
|
Everyone needs to decide how far is far enough for them depending on past, present and future employment plans, how their family communicates and so on. You can always use nicknames or alternate names to keep in touch and compartmentalize. Keep in mind that what is reasonable for one person is often ridiculous for another and vice versa.
Cache | December 17, 2016
|
I encourage you to think in terms of compartmentalizing instead of “disappearing.” The government saves huge amounts of data, but understands very, very little of it. As long as any red flags that would get your data analyzed lead back to someone else or to an identity that cannot be linked back to you, you don’t have much to worry about. This requires absolute discipline in following compartmentalization SOP, but is far from impossible.
The other thing to keep in mind is who you are hiding from. The vast majority of survivalists have not done anything to warrant spending a lot of money to have analysts comb through their personal lives, have undercover agents try to win their trust or to have operators break into their homes. Most of them are more concerned about criminals and marketers and just don’t want loads of any more data out there than necessary because they understand that it could be used against them one day, either by street criminals or the worst sort of criminals who wear ties.
Mahatma Muhjesbude | October 25, 2016
|
Excellent info, Cache.
If you’re starting ‘new’ on optimal on line privacy, remember that most of what you had on line BEFORE you went ‘dark’, will still be there. And once they link to your real name, it’s just a matter of time before you are located based on your ‘national ID card’ (REAL I.D. act of 2005) which Hitlery will make certain gets immediately fully implemented not long after she’s in with some hold out states.
What I’m trying now is first to get off all social media which I’ve done, and then hire one of those companies to ‘disappear’ any info possible related to my real identity. That might be hard, considering how much might be out there in many year old on line presence, but it might help when Hitlery’s Gestapo starting collating potentially ‘severe’ anti-Totalitarian regimes, like her new third Reiche will doubtless be.
Then I’m going to get a new computer paid for with cash (while we still can use cash) and last time i bought one they never asked to see an I.D. and only wanted a phone number which could be ‘mistakenly written’, and then your ‘alternate’ name and address. Which also can be somewhere ‘else’ from where you lay your head so it doesn’t matter if the ‘know’ the IP address.
Those are only the server’s direct location, and then from there they would track out to the subscribers from the other purchase info.
Then, you follow all your incryption and security advice and that should be about as ‘good as it gets’ if you want to be as low down on the ‘domestic’ terrorist watch list when Hitlery begins the gun confiscations, and then removes ALL other 4th/A privacy rights, to complete the totalitarian installation foundation.
Once They take away all your power of resistance, and all your privacy so they know everything about you and control it absolutely… it’s called enslavement.
Also, Cache, since you’re a world traveler and associate with ex-pats, what do you think would be the best ‘place’ these days? I’m checking into a few of them at the moment, Belize I don’t like, what do think about Panama, I’m looking at at a ‘deal’ that is almost too good to pass up? Just gotta do a forensic on their G.
Mahatma Muhjesbude | October 25, 2016
|
Oh, P.S. Last time I checked it was not ‘illegal’ to not reveal your name or use a different one for PRIVACY security purpose. That’s why celebs check into hotels with fake names, why writers use ‘pen-names’. and Muslims change their names to Mohammed on their I.D. cards. The essence of the 4th/A protects your privacy and also allows you to exercise that protection.
The only time using an alternate I.D. becomes illegal if you are using it to criminally defraud or in relationship to some other crime. And of course, in government business.
Of course, you know Hitlery will change that soon after she takes the power of the throne.
Cache | December 16, 2016
|
There are some factors to consider for an ex-pat hidey hole … Do you care if the country has an extradition treaty that they will honor? What is your budget? Do you want dual-citizenship? Consider your family situation and if it likely to change … are you single or married? Do you have family in another country already or were you born in another country. What languages do you speak or are you willing to learn? Do you want to stay in this hemisphere? What is your time frame? That last one can make a HUGE difference. If you are in a hurry, there are countries like Saint Kits & Nevis that essentially let invest in their country in exchange for dual-citizenship, so if it is important enough to you to drop upwards of a couple hundred grand on dual citizenship, then you can get it done relatively quickly. So, depending on your situation, St Kits & Nevis is a place to look at if you are in a hurry. Brazil doesn’t extradite it’s own citizens if you get dual citizenship. … there are just a lot of things to consider. If you want to speak privately, you can email me at this masked email: [email protected].
As far as alternate names vs aliases, the distinction is moral, not legal, but good guys have alternate names, stage names, pen name and traveling names and criminals have aliases and street names. There are certainly legitimate reasons for an individual to have and use alternate names and ways to establish them, such as adding them to a PO Box and requesting additional bank cards, press credential, etc. You can even have “shelf” identities … ID’s that are shelved, but read to go should you need it. Another measure is to keep an ID-making kit in your exit strategy cache. As long as you don’t apply for credit or deal with the government, etc. you should be OK. There are many folks who have known me for years only by alternate names.
Cache | December 16, 2016
|
Also keep in mind that this article is a heavily edited snippet from another project. In it’s original form, there was a lot more information presented in a somewhat different context than you see here. It’s hard to much with privacy in 600 words ; )
Not using, getting rid of or scaling back social media use is very important. Each individual needs to decide what is too much exposure for them and how much value they place on privacy. What you do, have done and plan to do for a living all factor in, as does how comfortable you are with a given level of risk. Philosophies really differ on that one. Those of us who understand that our right to privacy was paid for in blood and treasure value privacy highly. Others stand in line to give it up for some small measure of convenience … early adopting new technology before consequences are fully understood.
I truly believe that future generations will refer to this as the “pre-encryption era.” Once people understand the the liabilities of not encrypting, encryption will be a “default setting.”
bill in idaho | October 27, 2016
|
A Truly Splendid and Useful Article – it covers ALL of the Essentials ! I will refer to it Often. Thank You.
Cache | December 16, 2016
|
Thanks! and thanks for reading and commenting!
Anne | October 30, 2016
|
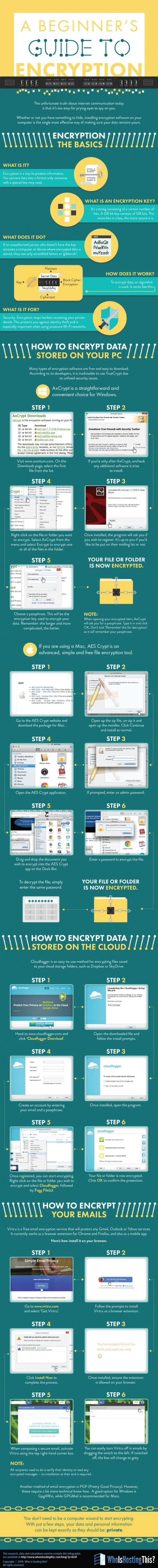
That big infographic looks like it has a lot of good information in it. But how do I print it? If I can’t print it, with the pieces the right size to read, it’s wasted for me. Got a suggestion?
Cache | December 16, 2016
|
Thanks for reading : ). Just right click on the image and select .
rick | December 16, 2016
|
Linux?
Cache | December 16, 2016
|
This article was part of another longer work and oriented toward Survivopedia’s average reader.
If you are truly serious about privacy, Linux is the last bastion. Microsoft & Apple OS’s and factory phone OS forks are rife with balloonware and marketing trackers. If you want a device to be fast and secure instead of offering lots of toys, games and features most folks don’t need, run Linux and root your phones. There are more devices running Linux than any other OS. If you haven’t, check out Tails. USB drives running Tails are a great way to compartmentalize.
https://tails.boum.org/
I am also working on a fire and forget SOS USB/MicroUSB OTG … just plug it into a phone or computer and it will use any available comms to get the word and your location out. There are some really tiny phones now, too.
Rick | February 8, 2017
|
I’m what most ‘preppers’ would call well left of liberal, but I am also concerned about the power of technology to impair freedom and individuality and its increased use by government and corporations. It saddens me to see like-minded people divided by the “us vs them” dialogue which been a VERY effective means of dividing and controlling us. Why diminish the number of allies with demeaning remarks like those in the LED info? Other than that, thanks for the needed help.
Pingback:Net Neutrality And The Law of Unintended Consequences | Survivopedia | December 21, 2017
|
Matthew Davids | July 28, 2022
|
Great article, thank you. How do I know if I have a spy app installed on my phone? I recently came across this article: https://celltrackingapps.com/spy-on-tiktok/, and now I’m suspicious that my wife could spy on me at TikTok. Thanks in advance for your help.